* 22 entries including: Cold War (series), Arizona road trip (series), Smithsonian makes 3D models, stochastic approach to climate modeling, malware versus smartphones, IBM TrueNorth neural chip, concealed transportable weapon systems, prospect of an end to AIDS pandemic, helicopter carriers, and French interventions in Africa.

* NEWS COMMENTARY FOR SEPTEMBER 2014: The crisis in Ukraine continues to sputter along; although the Ukrainian government had felt it was getting the upper hand over the rebels, the Russia government increased the pressure in response. Ukrainian forces, fearing a Russian invasion, were forced back on the defensive.
NATO is finally starting to respond, setting up a rapid reaction force that will be able to move to Eastern Europe should a crisis arise; it will not be big enough to greatly inconvenience the Russians if they decide to take action, but it let them know they're taking on what will become a big fight if they do. That was expected, but somewhat more surprisingly, in mid-September a small NATO exercise was conducted in western Ukraine -- involving 1,300 troops from 15 countries, including the USA. Obviously, the exercise sent some sort of a message to Russia, but the US stated it had been planned before the current emergency began.
BLOOMBERG BUSINESSWEEK reports that the West has a very powerful tool that could be used to exert pressure on Russia: the "Society for Worldwide Interbank Financial Telecommunication (SWIFT)", with headquarters in Brussels. It is not a government organization, instead being a cooperative run by banks. SWIFT operates a secure messaging system for moving money across borders, being the primary conduit for international financial transactions; it processes trillions of dollars every day for its 10,500 member banks, in more than 200 countries. If Russia were expelled from SWIFT, it would play hell with Russian trade and investment. Under an order from European Union authorities, SWIFT cut off Iranian banks in 2012; Iranian negotiators have consistently placed SWIFT exclusion on the top of the list of sanctions to be revoked.
Exclusion from SWIFT will not cut Russia off from all international financial transactions, since Russia could then improvise an international network to continue transactions. In fact, it is believed that Russia is helping Iran flaunt SWIFT exclusion, mediating transactions that are difficult, at best, to trace. The Russian government is now overtly taking measures to set up alternate transaction mechanisms. Still, such improvisations cannot match the security and volume provided by SWIFT membership -- and SWIFT membership rules strictly forbid member banks from working against the system, with banks that do vulnerable to government sanctions.
SWIFT exclusion isn't going to happen right away; it's effectively the financial equivalent of "going nuclear", and it would play hell with international markets. Russian attempts to evade the exclusion would also demand a lot of effort to monitor. Still, the option remains on the table, should all else fail.
* As reported by an article from TIME.com ("Why India's Modi and Japan's Abe Need Each Other -- Badly" by Michael Schuman, 2 September 2014), at first sight, there may not appear to be much similarity between India and Japan -- but a five-day visit of new Indian Prime Minister Narendra Modi to Japan in early September, with Japanese Prime Minister Shinzo Abe playing host to the visitor, underlined that the two countries have mutual interests: democracy, economics, and most significantly an assertive China on their respective borders. Modi said in a statement that his visit would "write a new chapter" in Indo-Japanese relations, while Abe commented in a press conference that bilateral ties between the two nations have "the most potential in the world."
There is big potential on the economic front. Japan and India are the second and third largest economies in Asia, respectively, but trade between the two was only $15.8 billion USD in 2013 -- just a quarter of India's trade with China. Japanese direct investment in India totaled $21 billion USD between 2007 and 2013, making Japan an extremely important investor for the country; but recently, the inflows have tapered off due to India's economic slowdown, with Japanese firms investing more in Vietnam and Indonesia than India. However, Modi is trying to revitalize India's economy by fixing its shabby infrastructure, strengthening its manufacturing base, and building a network of "smart" cities across the subcontinent. Japan's money and technological expertise will be extremely valuable in that effort, while Japan's sluggish economy can use the boost of Indian business -- all the more so because Japan's economic ties with China have been drying up, as Japan and China continue to bicker over a few lumps of rock in the East China Sea.
India has its own issues with China, and so Japan and India have motives to create a strategic partnership. The two leaders announced joint naval exercises and collaboration on defense technology -- China wasn't specifically named, but Modi all but did so when he said: "Everywhere around us, we see an 18th century expansionist mindset: encroaching on another country, intruding in others' waters, invading other countries and capturing territory."
China didn't fail to notice, with an editorial in the state-run GLOBAL TIMES sneering at the Tokyo summit: "The increasing intimacy between Tokyo and New Delhi will bring at most psychological comfort to the two countries. If Japan attempts to form a united front centered on India, it will be a crazy fantasy generated by Tokyo's anxiety of facing a rising Beijing."
* As reported by BBC.com, in the course of the recent hostilities in Gaza between the Palestinian Hamas movement and the Israeli Defense Forces (IDF), the outgunned Palestinians have gone literally underground to fight back, building elaborate tunnel complexes.
Tunnel-digging began in the 1990s, originally to smuggle weapons into Gaza from Egypt. Over time, the effort expanded to include smuggling of all types of goods, with the number of tunnels expanding from dozens to hundreds. The Hamas government obtained much of its revenue from the smuggling; however, after the Egyptian military suppressed the Muslim Brotherhood government, the tunnel connection was shut down, helping to fuel an economic crisis in Gaza.
From 2001, the Palestinians began to use tunnels for offensive operations against the IDF. Originally, they performed traditional mining, setting off explosive charges in tunnels dug beneath IDF outposts, but that required a great deal of effort for limited effect. In 2006, the Palestinians changed tactics, digging a tunnel underneath the Gaza-Israel border to allow an assault team to attack a border post from the rear.
That proving more satisfactory, Hamas began work on a complex of underground concrete bunkers connected with tunnels, with multiple entrances and exits, underneath the residential areas of Gaza. These underground complexes are similar in concept to the Viet Cong tunnels dug beneath the jungles of South Vietnam -- though the quality of finishing is better, with concrete walls and ceilings, electricity, and other amenities for lengthy occupation. The soil of Gaza is generally soft, and without the use of concrete, the tunnels would tend to fill in quickly. To hide the tunneling from Israeli intelligence, the entrances are usually located on the bottom floor of houses, mosques, schools or other public buildings. The removal of dirt and supply of materiel to a tunneling site is performed very discreetly.
The smuggling tunnels under the border with Egypt tended to be wide enough to handle transfer of bulky goods. The infiltration tunnels extending from the Gaza complexes, in contrast, are only wide enough to allow armed fighters to move in single file. Many of the tunnels are interconnected, with multiple camouflaged openings to emerge above ground in different locations. Palestinian fighters can pop up out of the ground to attack IDF units, and then disappear again. The entrances and parts of the tunnels are booby-trapped to discourage pursuit.
After the failure of Hamas' rocket attacks to inflict significant damage on Israeli towns in November 2012, they decided to ramp up their offensive-tunnel capability, to allow them to infiltrate assault teams into Israeli villages near the border. The IDF got wind of the plan, but was unable to do more than inconvenience it. Detecting tunnels requires either detecting the entrance to the tunnel or "seeing" the tunnel itself with various acoustic, seismic or radar detection devices. The tunnels are deep, typically about 20 meters (65 feet) below ground, and hard to spot. The tunnels are built mostly by hand labor, since the sounds of power tools might give them away.
Destroying a tunnel complex is troublesome; simply blasting the entrances and exits leaves most of the complex intact, allowing the Palestinians to dig new connections to the intact tunnels. That means that IDF engineers have to completely map a tunnel system, then lay explosives to destroy it all. In the meantime, the Palestinians continue to expand their tunnel network elsewhere.
COMMENT ON ARTICLE* ARIZONA ROAD TRIP (11): Having finished at Wildlife World, I then made my way back south to the freeway, getting some lunch on the way -- at a McDonald's in a Walmart, having petty misadventures with the staff -- and cruised to Mesa, on the opposite side of the Phoenix metro area, to visit the Commemorative Air Force museum there. It was an easy drive; given the size of Phoenix and the complexity of its freeway network, I had feared getting sidetracked, but I had no real problems. I liked the various interchanges; I realize they're likely monstrous to have in one's neighborhood, but I enjoy their soaring curves, and I like to negotiate them -- it's sort of like being on an oversized theme-park ride. Another nice feature was that they were made of desert pink concrete.

I canvassed the Commemorative Air Force museum very quickly. I wasn't expecting too much, just a handful of good condition warbirds, but they had a very spiffy MiG-21 that was worth the visit in itself. That done, I went to the Arizona Museum of Natural History not too far away. I wasn't expecting much there -- but I was also pleasantly surprised, since it had nice dinosaur statues and fossil displays, plus an impressive three-floor diorama. It was a quick trip, but worth the time and money.

Having gone through the Museum of Natural History in a flash, I knew I would be going past the Phoenix Zoo as I headed west through town on the way to Interstate 17 to Flagstaff. I checked my watch and decided, as long as I was in Phoenix, I might as well make a quick trip to the zoo, though it would mean getting to bed a bit late. I got off the freeway, found the zoo with little problem, parked, and set my stopwatch, giving myself one hour there.
It was consequently another quick trip, but the place is pleasant enough, being a fairly typical larger municipal zoo. I didn't see that much new to me, but I got good shots of otters; an Andean spectacled bear; a reclining tiger; and watusi cattle in a savannah environment. The zoo had a nice walk-through enclosure for squirrel monkeys, but alas the monkeys were lying low and I couldn't get shots of them. In any case, when I got out of the zoo the stopwatch read 55 minutes; I was promptly back on the road, heading north to Flagstaff.

* Now that all my touristy activities for the trip were done, I reflected on my foot condition, and realized that I wasn't any more footsore than I was from normal activities -- a far cry from the beaten-up condition my feet had been reduced to by my 2012 San Diego trip. I think it was just a question of making sure I paid attention to foot care and didn't let problems accumulate.
Night had fallen by the time I got to Flagstaff, and there was a sharp chilly wind blowing, a real contrast to the heat I had been enduring in the south. I got things kitted up and arranged as best I could to take off in the morning. While I was running back and forth from my room to the car, I was in the elevator with a couple, the guy having a clearly expensive Canon digital SLR camera slung over his shoulder. I told him: "That's some impressive camera firepower you've got there."
He grinned. "Thanks. I take pictures for a living, so I need a fancy camera."
"I've occasionally thought of buying a digital SLR, but for now fixed-lens cameras are about as much as I can handle."
"Oh, I make very good use of this."
As I left the elevator I replied: "No doubt -- but it also keeps you buying lenses all the time." He laughed. I finally got to bed, as expected somewhat late, which was problematic since I had such a long drive come the morning. [TO BE CONTINUED]
START | PREV | NEXT | COMMENT ON ARTICLE* THE COLD WAR (39): The near-irrelevance of the war in Korea from the strategic point of view was underlined on 1 November 1952, when the US tested the first hydrogen bomb on an island in the Pacific, the weapon proving to have a yield roughly a thousand times greater than that of the Little Boy bomb dropped on Hiroshima. The device used in the MIKE test was nothing that resembled a practical weapon, but it quickly led to combat-ready devices. Within ten months, the Soviets would test their own H-bomb, though it was dismissed by Western physicists as something of a fake, a fusion-boosted fission bomb, not a true fusion bomb. No matter: the Soviets would test their own "true" fusion bomb in another two years. The British were continuing their efforts to keep their hat in the nuclear arms race, detonating their first atomic bomb, a fission weapon, in the South Pacific on 3 October 1952. A British fusion bomb was in the works.
The race for delivery systems continued as well. The US was fielding the sleek Boeing B-47 jet bomber in numbers, with the lumbering B-36 being gradually relegated to the reconnaissance role. Stripped down, a B-36 could fly at altitudes a Red interceptor couldn't hope to reach, and the "Magnesium Cloud", as it was nicknamed, was used on spy flights over Communist countries.
The B-47s couldn't reach the population centers of the USSR without operating from forward bases overseas, but Boeing was developing a more capable follow on, with the eight-jet "B-52" performing its first flight in April 1952. The Air Force's Strategic Air Command was also acquiring a fleet of mid-air refueling tankers to give the bombers global range. The US Navy, determined not to be eclipsed by the Air Force in the strategic arena, had fielded a prop-driven carrier-based nuclear bomber, the "AJ Savage", with better jet bombers in the works.
The Soviets were working to catch up, performing initial flights of the Tupolev "Tu-16", with twin turbojet engines and comparable to the B-47, and the Tupolev "Tu-95", with four huge turboprops engines and comparable to the B-52; NATO gave them the handy reporting names of "Badger" and "Bear" respectively. The Tu-95 was the first Soviet bomber with true intercontinental range, placing the continental US under threat; the name "Bear" would prove most apt, since it would become a symbol of Soviet air power. Ironically, the "Bear" was a design descendant of the Tu-4 Superfortress copy, which meant that it had its roots in an American aircraft design. The Soviets were tinkering with mid-air refueling, but unlike the Americans would never heavily rely on it.
The British were working on jet bombers as well, developing a series of "V bombers": Vickers Valiant, Handley-Page Victor, and Avro Vulcan -- to deliver the nuclear weapons then being built by the UK. Work on long-range rockets was also in progress in West and East; the Soviets, having built their own V-2 clone as the "R-1", developed a "stretched" derivative designated the "R-2". Not to be outdone, von Braun's Germans, working at the Redstone Arsenal in Alabama, were developing their own improved V-2 follow-on, appropriately named the "Redstone", for his US Army employers. Neither had remotely intercontinental range, nor were they very accurate, but they pointed the way towards better rockets.
The competition to develop improved nuclear weapons, and their delivery systems, was picking up pace -- even as the realization was settling in ever more solidly that the Bomb could never be used in any but the most apocalyptic scenario. The hydrogen bomb had strongly underlined that conclusion: if fission bombs were mad overkill, fusion bombs were overkill squared. Ironically nuclear weapons, though at the center of Cold War strategic thinking, were only strategically relevant to the extent they maintained the superpower status quo. Any attempt to use them to alter that status quo posed an unpleasant prospect of global cataclysm. [TO BE CONTINUED]
START | PREV | NEXT | COMMENT ON ARTICLE* WINGS & WEAPONS: A note here in the spring discussed the sighting of mysterious flying-wing aircraft at high altitude over Amarillo, Texas. An essay by David Axe in COMBAT AIRCRAFT magazine presented an intriguing, if purely speculative, theory of their nature.
In July, the US Air Force began their "Long Range Strike / Bomber (LRS-B)" competition, to develop a stealthy strategic bomber to replace existing bomber types from the 2020s, with up to a 100 LRS-B machines -- presumably designated "B-3" -- to be obtained. However, examination of the proposed budget profile for the LRS-B program suggests a near-term commitment to production, as if development had already largely been completed. The notion that the LRS-B will be fielded in a decade also suggests that the aircraft is in an advanced stage of development.
As another factor, aviation journalist Bill Sweetman has noted a large budget allocation for an undefined USAF program in 2008. In the absence of specifics, the money could be for anything -- Sweetman is noted for his inclination to shoot from the hip -- but the clues are tantalizing. In short, the LRS-B program may simply be a "lockout spec" for a machine that's already flying. It would seem a fair bet, given the activities at present, the mystery aircraft program will come out of the black in 2015.
* An article from JANES.com shined light on the US Army's enthusiasm for use of the Beech King Air / C-12 twin-turboprop business aircraft as a battlefield aircraft, focusing on one configuration known as "Communications Electronic Attack with Surveillance And Reconnaissance (CEASAR)", in service in Afghanistan. CEASAR is a King Air A200CT carrying the Raytheon AN/ALQ-227 electronic attack (EA) system as fitted to the US Navy's Boeing EA-18G Growler electronic warfare (EW) aircraft. The AN/ALQ-227 operates as both a communications intercept receiver and a communications channel jammer.
The CEASAR platform is not actually in Army inventory, however, being a "contractor owned / government operated (COGO)" asset, provided under contract to the Army by the Virginia-based Dynamic Aviation Group, which flies King Airs and Bombardier Dash-8 twin turboprop airliners. There's a long list of different King Air-based special mission configurations, nicknamed "funnies", including:
JANE's added in another note that Lockheed Martin is now integrating the "Vehicle And Dismount Exploitation Radar (VADER)", a ground surveillance system, to King Air 350ER aircraft. VADER provides high update rate, high resolution ground mapping to provide precision target location, with system software able to maintain long-duration tracking of ground vehicle movement and behavior. According to JANE'S, by 2017 the Army wants to have a fixed-wing intelligence, surveillance, and reconnaissance (ISR) inventory of:
The Army will also field nine Bombardier Dash-8 Airborne Reconnaissance Low (ARL) platforms, replacing the earlier Dash-7 ARL platforms.

* As also reported by JANES.com, King Air 350ER special mission "funnies" are not only in service with the US, but also Australia, Colombia, Iraq, Japan, Saudi Arabia, Switzerland, and the UK. To service this market, Boeing is now flying their own Super King "funny" demonstrator, the "Reconfigurable Airborne Multi-Intelligence System (RAMIS)".
The RAMIS features a fairing on the back for a SATCOM antenna; defensive countermeasures; a retractable imaging turret under the extended nose; a "canoe" fairing under the belly for operational payloads; and a "farm" of blade antennas, including four antennas under the tail. The RAMIS is a modular system, obviously developed with the US Army requirement in mind, though attractive to other buyers. The current RAMIS configuration has a wide-area imager in the belly canoe, and may have a synthetic aperture radar and signals intelligence gear; other possible payloads include laser radar, foliage-penetrating radar, communications relays, or hyperspectral sensors.
COMMENT ON ARTICLE* SMITHSONIAN DOES 3D: As reported by an AP article ("Smithsonian Makes Push in 3D Imaging of Artifacts" by Brett Zongker, 13 November 2013), the Smithsonian Institution in Washington DC is one of the world's great museum, with a collection of 137 million items. Alas, there is no way to put all these items on display, and no visitor would be able to inspect more than a tiny fraction of them if they were.
Smithsonian officials think there's a way to extend the museum's reach, having initiated a 3D scanning and modeling effort to make virtual representations of its collections available to schools, researchers, and the general public all over the world. A small team is now modeling some of the Smithsonian's most significant items, including the Wright brothers' first airplane, Amelia Earhart's flight suit, casts of President Abraham Lincoln's face during the Civil War, and a Revolutionary War gunboat. Less familiar objects being digitized include a former slave's horn, a missionary's gun from the 1800s, and a woolly mammoth fossil from the Ice Age. The Smithsonian also provides an online viewer to allow inspection of the models.
According to Smithsonian digitization director Gunter Waibel: "Historically, museums have just tried to push data out. It's been a one-way street, Now museums are really rethinking their relationship with their audience, and they're trying to empower their audiences to help them along whatever learning journey they're on."
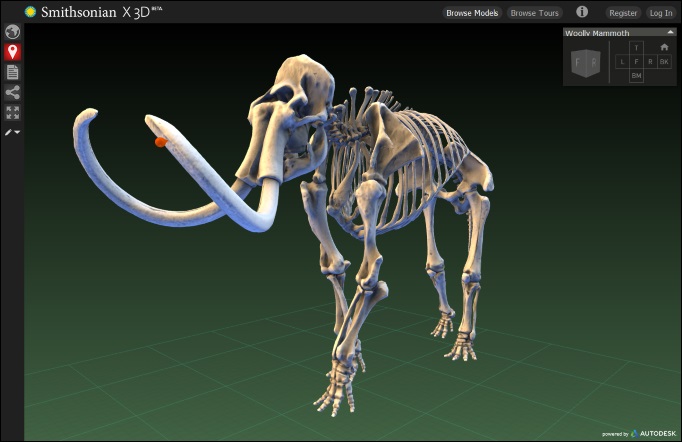
Waibel added that with the cost of 3D scanning and printing equipment declining in recent years, there's a new opportunity for museums to transform how they collect, curate, and conserve artifacts, and also how they educate. 3D models can help tell stories and create more engaging lessons. Smithsonian educators are building interactive online tours based on 3D models. For the 3D model of the Wright Flyer aircraft from 1903, they have created hotspots to help explain its engine and wing design, and the user can rotate the object in all directions for a closer look. Similarly, Smithsonian exhibits on public display could be boosted by the use of "augmented reality" to allow visitors to probe into specifics.
So far, the Smithsonian is allocating about $350,000 USD annually to 3D digitization, with companies also donating equipment. Museum officials are now working to raise $15 million USD to move the 3D lab from a suburban warehouse in Maryland to a new innovation center planned for the National Mall. There's no prospect of digitizing all of the Smithsonian's huge collection; the rate at which items are added to the database will depend on funding, as well as cost and effective utilization of digitizing technology. The Smithsonian has engaged private partners, and may even recruit volunteers to help.
A strategic plan drawn up in 1927 called for the Smithsonian to have an office in every US state, but it didn't happen. Thanks to digital outreach, the museums could actually realize that dream, with the potential to reach billions of people. Other museums have already started digitizing artworks or making 3D scans of sculptures. In New York City, the Metropolitan Museum of Art recently appointed its first digital director. There may come a time when, in the virtual world, 3D models will be commonplace.
[ED: One particular benefit from my point of view is that 3D modeling systems are easy to exploit for illustrations: just set up a view and do a screen dump to obtain an image bitmap file. Not only might an owner have trouble determining the origin of the image -- particularly if it's tweaked a bit, which is usually necessary anyway to get a workable illustration -- but copyright holders of a model don't have that much incentive to object to use of dumps of a model. Their business is making models, not illustrations, and if an illustration is properly credited, it's just promotion for their model.]
COMMENT ON ARTICLE* STOCHASTICS FOR CLIMATE MODELING: As discussed in an article from AAAS SCIENCE ("A Touch Of The Random" by Colin Macilwain, 13 June 2014), computer climate modeling has traditionally been based on brute force. A typical climate model cuts the Earth's atmosphere into a 3D grid of box elements, say 100 kilometers on a side and 1 kilometer high. Equations then determine conditions in each box as driven by sunlight and the conditions in neighboring boxes.
Such climate models are sophisticated, but they have fundamental limitations. One is that they weren't invented to predict future climate, but to assess the operations of the Earth's climate in the present. As a result, although they can give good clues to long-range climate changes, they don't yield specific details. New factors have been added to enhance their detail, but their limitations remain.
In addition, adding in factors increases the burden on computing power, which is strained by the nature of the models in the first place. A good climate model requires a relatively small cell size, which means a lot of cells and a corresponding load on computing power. Halving the size of the cells means eight times the number of cells, and at least eight times the computing power. In the 1970s, cells were 500 kilometers on a side, compared to 100 kilometers today; such a number of cells could not be handled by the computing hardware of an older generation. Climate researchers are looking down the road to 10 kilometer grid spacing in a decade -- but ever more powerful computers end up consuming ever more power, with projected supercomputers requiring powerplants of their own that could otherwise provide electricity to a good-size town.
Ironically, there's already software for weather prediction that could, in principle, address these difficulties. Starting in the 1990s, researchers at the European Center for Medium-Range Weather Forecasts (ECMWF) at Reading in the UK began to incorporate "stochastic" methods in their weather forecast models. Known less gratingly as "Monte Carlo" methods, they were first used in a big way by physicists working on the development of the atomic bomb in World War II to model the diffusion of neutrons through materials. The researchers had struggled to find a deterministic way to model the process, to finally realize that they could do the job much more easily by leveraging off random chance.
For a trivial example, consider using a stochastic process to calculate the value of PI. Suppose we have a square with sides of unit length, and have a circle with a diameter of unit length embedded in it. We then use a random-number generator to produce a set of points within the square; we count the total number of points, and the number of points that fall within the radius of the circle. The ratio of the number of points within the circle to the total number of points then gives an approximation of the area of the circle, which can used to determine an approximate value of PI.
This is a simple-minded example; we have much more efficient ways of calculating the value of PI, but it does show how generation of random values could be used to perform a calculation. Of course, the more random values generated, the better the approximate solution. Where stochastic methods come in handy is in models that require an enormous amount of number-crunching if performed in a deterministic way; stochastic models, in effect, simply leverage off samplings scattered at random through the data space in question to perform the calculation, with the accuracy of the result improving with the number of samples. Climate models are a good fit for the stochastic approach, otherwise demanding massive computing power, and with useful results only having a few digits of precision -- the error bars on the data render any more precision useless.
Stochastic methods are now being used in physics and engineering, even by insurers. The ECMWF modelers began with conventional weather forecasting models and ran them with random variations in initial conditions, an approach known as "ensemble modeling". By summing the results, they obtained better forecasts. ECMWF researchers believe their work has significant implications for climate modeling. For example, tropical thunderstorm systems can release total energy comparable to that of a hydrogen bomb, meaning they have a clear effect on the broader climate system -- but they have cores only a few kilometers wide, beneath the resolution of traditional climate models, and it has proven difficult to fit thunderstorms in. Advocates of stochastic methods believe that their approach would give better results while placing less burden on computing power.
There's considerable excitement over the idea of using stochastic methods in climate modeling, with a range of experiments in progress. One notion is to replace deterministic subroutines in existing climate models with stochastic equivalents; such an experiment was performed with a model from the US National Center for Atmospheric Research, and gave excellent results. That's all for the good, but advocates believe that such an incremental approach is too limited. Tim Palmer, a physicist at the University of Oxford in the UK who has directed ECMWF work, says: "Ideally, I think we will need to go back and design the models from scratch. You really want to build the stochasticity in at a fundamental level, to make it more consistent with the underlying laws of physics."
Some climate researchers are even advocating climate models based on purely statistical and stochastic approaches -- but others are applying the brakes, saying that while stochastic methods are interesting, there's no consensus just yet that they can or should replace traditional modeling. Advocates shoot back that climate modeling is heading for an inevitable computing crunch, and that without a change in mindset, climate modeling is on a dead-end street.
The debate can be resolved by experience. Ben Kirtman, a climate scientist at the University of Miami, says that the climate modeling community needs to be "unforgiving" and make "hard-nosed comparisons" of the predictive power of climate modeling: "I think we still have an enormous amount to learn."
COMMENT ON ARTICLE* ARIZONA ROAD TRIP (10): I got up on the morning of Sunday, 13 April, ate breakfast at the hotel, and then hit the road north to Phoenix. I had a lot of things to do that day, so I was not wasting any time.
My first stop was Wildlife World, a privately-owned zoo in Goodyear, in the western suburbs of Phoenix. Navigation was straightforward, though I was looking for a Walmart or Target, having an item I needed to pick up. I was dressed in khaki pants and an overlarge long-sleeved Nike white sports shirt -- an expensive item I'd picked up in Loveland before I left, with fancy features like breathing holes under the armpits. It cost about three times as much as comparable long-sleeved cotton tee shirt, but it looked literally cool, and it certainly was comfortable. With the Nike logo on front, it gave me a feeling of something like a Starfleet uniform.
The one problem was that it was open at the collar, and I didn't want to aggravate the sunburn I'd picked up yesterday -- worrying about going from "mildly burned" to "severely burned". I figured I'd buy a bandanna and safety pins, wrapping the bandanna around my neck and tucking down the shirt collar to keep the Sun out. I found a Walmart a few miles from the exit on the freeway to Wildlife World and found a selection of bandannas. I was hoping for white or light pastels, that being the most proof against sunlight, but all they had were black and bright colors. I finally settled on medium blue.
Properly kitted up, I got back on the freeway and took the hop to the exit to Wildlife World. Goodyear is a growing suburb; according to Wikipedia, it was established during the war by the Goodyear company to grow cotton needed for fabric reinforcement of tires. There were plenty of new housing developments, and as I drove down the streets I had to marvel at how pretty it was, even though lawns were rare. They got by with dry-climate trees and shrubberies, and they were very bright in their flowers and the sun. Arizonans seem particularly fond of the palo verde tree, which generates a riot of yellow flowers. I suspected later that I was getting the best view of things, however; spring was a good time to visit, since everything was in bloom.

After some minor difficulties with freeway construction -- Wildlife World's website had warned about that, but hadn't made it very clear, though I wasn't significantly delayed -- I drove in and parked. While I was headed to the entrance, I noticed a license plate titled: DUCKIE. Huh? I had to take a picture of it. In doing so, I thought I might make a hobby of snapping vanity plates, at least the ones that made any sense. It would be little effort and might draw more attention to my Flickr account.
There were parrots on a perch as I entered the gateway building; parrots would turn out to be something of a motif of the facility. At the ticket kiosk I was behind a young couple, and the guy was showing off a fancy piece of hardware on his wrist. I had to ask: "Is that a Pebble?"
"Yeah!"
"I've never seen one before."
"They're not common yet, I've only seen a few others myself."
"It communicates with your smartphone?"
"Uh-huh. It'll tell me when I get a message."
"Heh! YOU HAVE MAIL." He laughed. A gimmick, maybe, but certainly a cute gimmick.
There was an aquarium building near the entrance, which I went through quickly; it didn't make much impression on me. I was more interested in spider monkeys climbing trees on islands in the middle of a pond -- it seems they don't like getting wet, so they stay on the islands. I don't recall I'd ever seen spider monkeys in an open environment before.
Following that, I took a little toy train ride though a savannah environment; it cost four bucks, it was kind of a waste, since it wasn't a very long route, and there were plenty of good observing stations along the side of the environment. I got some nice shots, but I could have done just as much by walking around.

I went on to the new safari park extension, thinking it was going to be something extensive -- but no, though it was okay, it was more of the same. I didn't bother with the tram ride, simply walking around to the viewpoints. They had more islands with spider monkeys and capuchin monkeys. That done, I went back to the zoo proper and took a cable chair ride over a section of the zoo. That cost another four bucks, but it was worth it, since it gave me good camera views of the animals, and I picked up a fair set of shots.

There wasn't that much more there after that, however. Wildlife World turned out to be the one stop I made on the trip that was below expectations. I was expecting a commercial facility, but something more along the lines of Busch Gardens in Tampa, flashy and spiffy. In reality, it tended to the rough -- mostly dusty dirt pathways, not even gravel, with the decor of the facilities tending toward unpainted timber. There were also many dingy little cages, suggesting in part a "concentration camp for animals". However, it did have a nice collection, and they had plenty of open-air environments, notably the monkey islands, that were very creditable. On later inspection of the photo haul, I did fairly well for myself there, so I didn't feel ripped off; I was just expecting something prettier.

I wanted to stay to noon to catch the animal show, such usually being rewarding. It proved, however, as under-par as the rest of the operation. The bleachers were beaten-up and felt unsteady, and the presentations were not very interesting. They had an emu; an albino python; a desert fennec fox; a crested sereima, a South American bird something like a small secretary bird, a striding ground hunter; and a cockatoo. Incidentally, the staff explained why there were so many parrots and cockatoos there: such birds live a long time, people either cannot or do not want to care for them indefinitely, so Wildlife World acted as "rescue" organization.

The fennec did get my attention, since I'd never seen one before. They're nocturnal, it looked like it had been roused out of its sleep and wanted to go back to napping. It seemed very cuddly, which was another surprise, since I would normally assume that one is likely to lose fingers trying to pick up a wild animal. Its name was "Gizmo", which rang a bell -- oh right, the old Joe Dante GREMLINS movie, the gremlin Gizmo also having oversized ears. I took as many shots as I could since it seemed unlikely I would ever have such a good shot at a fennec again. The results were mixed on later inspection, camera auto-focus having troubles with fuzzy targets. I hadn't thought of that, or I would have tried some manual focus shots. Still, it ended a lackluster exercise on a high note. [TO BE CONTINUED]
START | PREV | NEXT | COMMENT ON ARTICLE* THE COLD WAR (38): POWs were the sticking point of ending the war in Korea. The problem was not really with the Communists on the POW issue, it was with the UNC. The coldly logical approach to handling POWs was for both sides to simply repatriate them. However, the South Korean government was not in favor of involuntary repatriation, for the reason that many of the prisoners held in South Korea didn't want to be sent back, including Chinese Nationalists who had been pressed into PLA service, and South Koreans who had been similarly pressed into KPA service. Similarly, Americans remembered the fate of Soviet nationals who had put on German uniforms during World War II, to be taken prisoner by the Americans and British -- and then handed back to Stalin, to be shot or sent to prison camps.
The two sides did agree to provide lists of POWs, but the results made nobody happy. The UNC found out that the number of prisoners listed by the Reds, about 12,000, was much smaller than their numbers of missing in action (MIA). To be sure, it was obvious that many of the MIA had been killed in combat operations and not accounted for; the suspicion remained that many prisoners had died of abuse in captivity, or been outright murdered. As far as the Communists went, they had estimated that about 170,000 of their own had been taken prisoner, only to be informed that the actual number in POW camps was about 130,000. What happened to the rest? The UNC said they were South Koreans who had passed loyalty screening and been released, which was not an answer that pleased the Communists at all.
Truman, being a man of conscience, had to come out against involuntary repatriation, announcing in January 1952 that no POWs would be returned against their will; he chose a "one for one" exchange process, which would favor the UNC because the numbers of UNC POWs was so much smaller. That made repatriation slower and more complicated, with the Communists doing all they could to make it even more complicated.
The UNC POW camps tended to be sorry affairs; there was generally enough food and other necessities for the prisoners, but they were badly run, sanitation being a major problem, and both the officers and men running them were typically rejects who weren't seen as any good for front-line units. There were serial sackings of officers and NCOs at some camps, while the camp guards tended towards a nasty combination of lazy and brutal. While the Chinese kept tight control over their POW camps, in UNC POW camps the prisoners, as a rule, did whatever they felt like within the bounds of the camp.
Communist leaders had ordered political officers to allow themselves to be captured; once behind the wire, they were to organize the prisoners to make as much trouble as possible, regardless of how many prisoners got themselves killed in the process, and see to it that prisoners who rejected Communist authority were dealt with appropriately. The logic behind that policy was simple: make keeping the prisoners so troublesome that the UNC would simply hand them all back wholesale. To compound the trouble, in some cases, Nationalist Chinese POWs that had been captured while in PLA service set up organizations of their own to make trouble and step on the independent-minded. Uprisings had begun in December 1951, ramping up into pitched battles, with some UNC troops and hundreds of prisoners killed.
In the spring of 1952, General Mark W. Clark took over from Matthew Ridgeway, who became NATO supreme commander in Europe. Clark couldn't have been too happy at the assignment, the static pattern of the war in Korea having been clearly set; nor happy at the fact that military command of NATO, an obviously more significant job, had been handed to Ridgeway and not himself. Clark still had his duties; he decided to take the camp uprisings seriously, immediately initiating Operation BREAKUP, to deal with them.
Uprisings were met promptly with force majeur, UNC soldiers using rifles and riot gas, backed up by armor, suppressing the uprisings at any cost. Chinese POWs were segregated from Koreans, the Chinese being sent to Cheju Island, the biggest island of South Korea; there, Chinese who were to be repatriated were further segregated from those who weren't, while Communist political officers were hunted down. The camps would never be entirely peaceful, but the Communist ploy had failed. [TO BE CONTINUED]
START | PREV | NEXT | COMMENT ON ARTICLE* Space launches for August 2014 included:
-- 02 AUG 14 / GPS 2F-7 (USA 132) -- A Delta 4 booster was launched from Cape Canaveral in Florida at 0323 GMT (previous day local time + 4) to put the "GPS 2F-7" AKA "USA 132" AKA "Navstar 71" navigation satellite into orbit. It was the seventh Block 2F spacecraft, with the Block 2F series featuring a new "safety of life" signal for civilian air traffic control applications. The Delta 4 was in the "Medium+ (4,2)" configuration, with a 4 meter (13.1 foot) diameter fairing and two solid rocket boosters.
-- 05 AUG 14 / ASIASAT 8 -- A SpaceX Falcon 9 booster was launched from Cape Canaveral at 0800 GMT (local time + 4) to put the "AsiaSat 8" geostationary comsat into orbit for the AsiaSat company of Hong Kong. AsiaSat 8 was built by Space Systems / Loral and was based on the SS/L 1300 comsat platform; it had a launch mass of 4,535 kilograms (10,000 pounds), a payload of 24 Ku-band transponders, and a design life of 15 years. AsiaSat 8 was placed in the geostationary slot at 105.5 degrees east longitude to broadcast direct-to-home TV signals to China, India, the Middle East, and Southeast Asia. It was co-located with the AsiaSat 7 comsat, launched in 2011. This was the 11th launch of the SpaceX Falcon 9.
-- 09 AUG 14 / YAOGAN 20 -- A Chinese Long March 4C booster was launched from Jiuquan at 0545 GMT (local time - 8) to put the "Yaogan 20" satellite into orbit. It was described as an Earth observation satellite -- but was observed to be a triple payload, possibly a "flying triangle" type naval ocean surveillance satellite, to track maritime traffic from their radio emissions. Similar spacecraft were launched in March 2010, November 2012, and September 2013.

-- 13 AUG 14 / WORLDVIEW 3 -- An Atlas 5 booster was launched from Vandenberg AFB in California at 1830 GMT (local time + 7) to put the "WorldView 3" Earth observation satellite into Sun-synchronous orbit for DigitalGlobe. The satellite was built by Ball Aerospace and was based on the Ball BCP-5000 satellite bus; it had a launch mass of 2,810 kilograms (6,200 pounds), the payload being a multispectral imager with 29 channels and a best resolution of 30 centimeters (1 foot). Design life was seven and a quarter years. It was the third WorldView satellite, and joined five other DigitalGlobe satellites in orbit. The booster was in the "401" configuration, with a 4 meter (13.1 foot) fairing, no solid rocket boosters, and a single-engine Centaur upper stage.
-- 19 AUG 14 / GAOFEN 2, BRITE PL 2 -- A Chinese Long March 4B booster was launched from Taiyuan at 0315 GMT (local time - 8) to put the "Gaofen 2" Earth observation satellite into orbit, the second of six such spacecraft for Earth resource observation. The launch also included the Polish "BRITE PL 2" smallsat, the last of six BRITE satellites to observe variations in the amount of light coming from the brightest stars visible from Earth. All the BRITE satellites were based on the "Canadian Generic Nanosatellite Bus", along the lines of a 1-unit (1U) CubeSat, but with dimensions doubled to 20 centimeters (8 inches) on a side; the bus was first demonstrated by the CanX-6 satellite, launched in 2008. Each BRITE satellite carried a three-centimeter (1.2 inch) CCD-based telescope and weighed about 10 kilograms (22 pounds).

-- 22 AUG 14 / GALILEO FOC-1 -- A Soyuz 2-1b (Fregat) booster was launched from Kourou in French Guiana at 1227 GMT (local time + 3) to put the first two fully operational Galileo navigation satellites into medium Earth orbit. Each satellite had a launch mass of 730 kilograms (1,610 pounds), and carried a secondary search & rescue radio relay payload. They were built by OHB of Bremen, with payloads from Surrey Satellite Technology LTD of the UK. The two operational satellites followed four validation satellites, launched in 2010 and 2011. The Galileo operational constellation of 24 satellites is to be in place by the end of 2017, with six spares bringing the total up to 30. Unfortunately, the two initial operational satellites ended up in lower orbit than planned; it was not immediately clear if they could boost themselves up to their proper orbit.
COMMENT ON ARTICLE* MOBILE MALWARE? Anybody who's technically literate fears malware, knowing how sneaky it can be. Of course, the smartphone is the latest frontier for cybercriminals -- but Babbage, THE ECONOMIST's technology blogger, pointed out in an essay ("The Threat In the Pocket", 18 October) that so far, it hasn't been much of a problem. More by accident than design, smartphones have turned out to be much tougher to infect and exploit than laptops and desktop PCs.
Makers of security software are raising the alarm, but of course they would. Corporate IT managers do have a real concern, in that smartphones carried into an office could be used as a "vector" to infect their otherwise secure internal networks. Such an attack would likely be very precisely targeted, with competitors or even foreign intelligence services attempting break-ins to obtain corporate secrets. Otherwise, for the time being, malware writers aren't that interested in smartphones. Researchers at Georgia Institute of Technology and Damballa, a security firm based in Atlanta, surveyed two networks with some 380 million users between them, to find less than 3,500 phones with signs of having been infected by malware -- not even one in 100,000. They extrapolate that only 15,000 smartphones of the 1.5 billion in the world today are carrying malware.
Why have smartphones proven a hard target? One reason is that most smartphone users do not pretend they are administrators; they use the functions the smartphone came with, or download and plug in new apps. Smartphone vendors typically discourage tweaking with the phone operating system, warning users that going much beyond downloading apps can not only void the phone's warranty, but can even "brick" the device, turning it into an expensive paperweight. If users don't need to -- don't want to, can't -- tinker with the system, malware writers have difficulties doing it as well. Yes, a handful of users do still tinker with their smartphones, opening them up to vulnerabilities, but the number is too tiny to make it worth the effort for malware writers.
A related reason why smartphones have so far remained largely free of malware is because they lead sheltered lives. When people want more apps -- the average per user is about 40 -- they usually get them from one of two official download sites: Google's Play Store for Android devices, and Apple's App Store for iPhones and iPads. PCs never had any such comprehensive centralization of applications distribution, and their security has suffered accordingly. Centralization pays big dividends: both the Play Store and App Store are policed; Apple is stricter than Google, but Google is still vastly safer than any other outside app site. Both sites have hundreds of thousands of apps, and so there's generally no need to go elsewhere. They don't provide porn or pirated music, of course, but anyone with sense who goes to sites that do can expect trouble.
Such mobile malware as exists tends to be more annoying than dangerous -- "nuisanceware", for example generating unwanted ads, obnoxious toolbars, or redirects to trashy websites. Sometimes it's "scareware", trumping up system problems and then offering to fix them, for a fee. Hardcore malware will collect personal data and monitor keystrokes; but since smartphones, unlike desktops and laptops, aren't generally used for financial transactions at present, malware writers aren't so interested. Given the emergence of the "electronic wallet" with near-field communications links, that's likely to change in the future.
Again, for right now it is only big organizations that are much worried about cellphone security -- but even they are less worried about targeted attacks than employees losing phones or having them stolen, the phones possibly containing critical information. That issue can be addressed using tracking and remote lock-out schemes, which are recommended to any smartphone user anyway. Corporate IT managers also need to educate employees not to bite on sneaky emails or fall for other malware tricks, but that issue is the same no matter what kind of computer is being used.
Will the sanitary smartphone environment remain sanitary? A skeptic would hesitate to say so; things may change abruptly and much for the worse. However, it doesn't seem to be happening just yet, and there remains the optimistic possibility that smartphones may be able to keep a step ahead of threats as they emerge.
* As discussed in a note in BLOOMBERG BUSINESSWEEK, millions of smartphone users have downloaded an app named "Plague INC" that sounds, on first hearing, as the ultimate malware, allowing users to create pandemics to infect the world.
Actually, it's a game, in which the players balance the factors involved in pandemics -- climate, population density, poverty, virulence and contagiousness of a disease, resistance of the disease to treatment, and so on -- in order to destroy humanity before a cure can be found. It sounds perverse, but the game's creator, James Vaughn, was invited to speak at the US Centers for Disease Control (CDC) in Atlanta, the CDC seeing the game as a way to educate the public about the threat of pandemics and the measures taken to deal with them. Vaughn has leveraged his CDC connection into the game, with mock news reports from the CDC popping up to track the progress of the virtual pandemic and the progress of countermeasures taken against it.
COMMENT ON ARTICLE* THINK TRUENORTH: As reported by an article from THE NEW YORK TIMES ("IBM Develops a New Chip That Functions Like a Brain" by John Markoffaug, 7 August 2014), IBM Research has developed an experimental chip named "TrueNorth" that uses neuromorphic technology -- inspired by the operation of the brain -- to perform computing tasks with very low power.
While much remains to be learned about the operation of the brain, it is known to be a matrix of nerve cells or "neurons". Our neurons are electrical cells, generating an electrical output signal in response to a set of inputs. Each neuron consists of a cell nucleus, surrounded by a branching set of filamentary "dendrites" for input, with a long threadlike "axon" for output featuring a set of tendrils at its end. Dendrites of one neuron are linked to the axon output tendrils of many other neurons, each link being through a gap called a "synapse". When the sum of electrical signals from other neurons reach a certain threshold, the neuron "fires" and drives an electrical signal down its axon to drive other neurons. The synaptic connections are "weighted", some adding more to the sum than others, some even subtracting from the sum; they are "programmed" by simple experience, becoming stronger the more they are activated. The brain's neurons are wired up through a staggeringly elaborate arrangement of synaptic connections.
TrueNorth contains 5.4 billion transistors, organized in 4,096 neuromorphic "cores" interconnected in a mesh network, with more than 400 megabits of on-chip memory, making up a million electronic neurons. Each neuron connects with 256 others through synaptic connections that can be individually programmed to set the "weight" of the signal between neurons, giving 256 million programmable synaptic connections in all. In 2011, IBM only had a prototype chip with 256 neurons.
Individual cores can fail, but the chip will still function, if at slightly degraded efficiency for each lost core. TrueNorth's "neural network" is roughly comparable in elaboration to the brain of a bee, but only draws 70 milliwatts of power. It can achieve low power because it doesn't depend on a central clock for its operation, its architecture being asynchronously "event-driven": neurons only operate when they get data, with data "spikes" propagating through the network in analogy with the electrical impulses of our brain's neurons. Multiple TrueNorth chips can be ganged up via external networks, IBM already having experimented with a 16-chip system. The research group is now working towards a system with 4,096 chips that will only draw four kilowatts of power.
While not well suited for calculations as such -- those can be farmed out to a conventional processor -- TrueNorth technology is good at pattern matching, with applications in video and audio interpretation systems. Dr. Dharmendra Modha of the TrueNorth research team comments: "The [TrueNorth] architecture can solve a wide class of problems from vision, audition, and multi-sensory fusion, and has the potential to revolutionize the computer industry by integrating brain-like capability into devices where computation is constrained by power and speed."
IBM's research was funded by the Pentagon's "blue-sky" investigation office, the Defense Advanced Research Projects Agency (DARPA)', under a program named "Systems of Neuromorphic Adaptive Plastic Scalable Electronics (SyNAPSE)". The practical application target of IBM's ultralow-power neuromorphic processors is to automate interpretation of surveillance performed by military drones: as the number of drones in the air increases and their sensors become more capable, the military is drowning in torrents of data. This problem is growing as humans in general as data streams of all kinds increase in number and magnitude; machines will increasingly need to sort through the data to only tell human end users what they need to know.
A secondary goal of TrueNorth is to investigate the workings of biological brains, with an eye towards the ultimate implementation of sentient machines. IBM is preparing to make TrueNorth available to universities, with the chip "ecosystem" including a neuromorphic programming language. TrueNorth will eventually get into the hands of commercial users for evaluation and development.
Not everyone has been impressed by TrueNorth. Yann LeCun, director of artificial intelligence research at Facebook and a pioneering expert in neural networks, expresses skepticism: "The chip appears to be very limited in many ways, and the performance is not what it seems." The capabilities in pattern recognition claimed by IBM researchers in their release paper, LeCun says, are nothing unfamiliar to "anyone in computer vision or machine learning."
Terrence J. Sejnowski, director of the Salk Institute's Computational Neurobiology Laboratory, disagrees: "The TrueNorth chip is like the first transistor. It will take many generations before it can compete, but when it does, it will be a scalable architecture that can be delivered to cellphones, something that [digital processors] will never be able to do."
COMMENT ON ARTICLE* ARIZONA ROAD TRIP (9): Having canvassed the aircraft and other machines on the flightline, demonstrations were beginning, starting with a jet-powered dragster -- a gimmick as far as I was concerned, not much more than a noisy toy. I was much more interested in a demonstration by Customs in which ground units and two helicopters intercepted a simulated gang of border traffickers, that being something I'd never seen at an airshow. That was followed by a small warbirds flyby -- a B-25 and a P-51 -- and then an aerobatics demonstration of four private fliers in Chinese CJ-6 trainers.

The Air Force then put extra effort into a "combat search and rescue (CSAR)" performance, with C-130s, A-10 Warthogs, and Black Hawk helicopters, attempting to extract a ground force team that had come under attack by insurgents. The A-10s were impressive, with pyrotechnics being used to simulate their strikes on the insurgents -- thanks to the camera burst mode, I got a good shot of a fireball, not easy to come by. I was also interested in the cloud of Arizona dust thrown up by the Black Hawks as they came in to land, demonstrating the difficulties of "brownout" conditions in operational environments.

I had to take notice of a cute little Mexicana girl on the shoulders of her dad, excitedly watching the show. I was impressed by the dad, who looked like a Mexican action movie star. I wish I'd ever looked half that studly.

That was the most of it. There were the usually corny aerial acts in between the interesting demonstrations; having been to many airshows, I tend to find attempts at aerial comedy and the like weak to the point of wearying. The Thunderbirds were to finish off the show, but I'd got photos of them the day before, and I wanted to beat the rush out the gate of the base anyway. I walked back down the flightline to my car. It was carpeted with dust, though I couldn't complain too much; some cars downwind of the avenue off the parking field were thickly covered. Most of the dust blew off my car after i got on the road, but there was still a thin film left.
After I got back to the hotel, I took some of the rags I keep in the car to clean off the dust. While I was wiping down the car, another car drove up nearby in the lot and parked. A teenage girl in a swimsuit and wrapped with a towel got out of the back, towing a chihuahua on a leash; the chihuahua was scoping me out, so I went over to see if he was friendly. I crouched down and held out my hand, but the dog backed up a little and eyed me warily. The girl told him: "Oh, why don't you be friendly, Potato?"
"Potato?" There must have been a story behind that name, but I didn't enquire as to what. The dog didn't take the encouragement, so I went back to cleaning up the car. Then I noticed a young couple walking down the parking lot, holding hands and talking animatedly. They got my attention: the guy was a twenty-something, on the positive side of ordinary, sort of like the male lead in a TV sitcom -- but the girl was not at all ordinary. She was petite, clearly below 45 kilos / 100 pounds, with skin the color of milk chocolate, hair the color of dark caramel in neatly-arranged curls under a cap, dressed in denim with short pants and wearing sandals. She looked like a black pop star, except for the fact that most of them don't look that good.
There was a certain mismatch between the two people that was puzzling. I didn't actually think for a few days that it might have been a commercial arrangement. I felt a bit stupid, but it's not something I see every day; the girl was vastly cute, not at all trashy; and they seemed to be enjoying each other's company so much that it gave no suggestion of being anything mercenary. On thinking the matter over, I realized I could come to no conclusion. Conjectures without data are of little value; for all I knew the girl, being slender, might not actually have been a girl -- don't ask, don't want to know. I could say one thing for certain: if it was a commercial arrangement, it was definitely an expensive one. That girl could name her price.
Anyway, I got done cleaning up the car, then went upstairs to try out the MBLite with the new flash memories I had bought. It was time-consuming, but I finally got all the photos backed up -- and got to bed, once again a bit late. [TO BE CONTINUED]
START | PREV | NEXT | COMMENT ON ARTICLE* THE COLD WAR (37): On the front lines in Korea, the wealth of UNC troops might not have seemed so evident to themselves, but it was clearly obvious in contrast to the poverty of Communist troops. They had no serious air support, their supply chain was far more limited, their medical resources were minimal, and leaves were granted only meagerly. Red forces, however, demonstrated impressive discipline and a willingness to fight against an enemy whose superiority in resources, particularly firepower, was painfully obvious. A balanced report from the Commonwealth Division -- composed of British, Canadian, Australian, and New Zealand troops -- gave a respectfully balanced assessment of the Chinese fighting man:
BEGIN QUOTE:
The Chinese infantryman is well-trained, well-equipped, and efficient. He is an excellent night fighter, very brave, with good morale, and good at finding his way in the confusion of battle. ... The Chinese are prepared to take casualties, and therefore can patrol in strength. There is little doubt that the war in Korea has been fought to suit the Chinese. His limitations in communications, his lack of air support, and absence of heavy equipment and vehicles would make him very vulnerable in a war of movement.
END QUOTE
While the Communists proved skillful at digging out impregnable positions along their side of the front lines, they also suffered from a lack of experience with static warfare and failed to grasp the need for good sanitation, particularly separation of latrines from water supplies. The result was widespread disease, notably typhus; Chinese leadership conveniently concluded that the disease was due to American biological warfare attacks, with "confessions" squeezed out of captured aircrew stating they had conducted such actions. Eventually, Chinese officers learned more about field sanitation, deaths from disease fell, with accusations of biological warfare declining along with them.
Although the KPA was notably harsh with UNC prisoners -- fond of beating them up, if they didn't kill them immediately -- the Chinese were, to a degree, conscientious in their treatment of POWs. Deaths among UNC prisoners were common early on, but that was more due to disorganization than deliberate malice. The Chinese had meager resources even for their own troops, and not much to spare for prisoners; hunger was the normal lot of UNC prisoners, with medical care being primitive when it was available at all.
Prisoners were also subjected to repetitive political indoctrination. It was entirely by rote, making an impression only on those who had brought the Red message with them into captivity, everyone else finding it merely a bore -- though the Chinese were able to prey on the inevitable insecurities of prisoners to undermine their morale. Prisoners were only pointedly worked over when the Chinese had a specific reason to do so, such as to obtain significant intelligence, or get the facts behind the "biological warfare" program supposedly being conducted by the Americans.
* The Chinese were not unique in their paranoia, anti-Communist sentiment continuing to grow in the West. The Soviets had built up a spy ring in Britain during the 1930s, focused on students at Cambridge and Oxfords, with some of them going on to significant positions. In 1951, a ring that became known as the "Cambridge Five" was uncovered, though only four of the members were positively identified:
The identity of the "fifth man", only known from his Soviet codename, is still debated -- one popular candidate being John Cairncross, who was deep in the British codebreaking organization.
In any case, the US National Security Agency, under a program named VENONA, had been decrypting Soviet messages, and got hints that MacLean was a Red agent. Philby, who had a high level of access to US intelligence, tipped off MacLean, who fled to the USSR with Burgess in May 1951. The defection led to suspicion against Philby, who was forced to resign from MI6 -- much to his exasperation, since he felt he had a good chance to become head of the operation. The evidence against him being lacking, he was exonerated, working as a journalist into the early 1960s, when evidence finally started to build up against him. He would flee to the Soviet Union in 1963. Blunt, under pressure, would confess and tell all he knew to the authorities, who kept his treason under wraps; Cairncross would similarly come clean, and remain a free man.
Philby would not enjoy his new life in the USSR. He wasn't trusted by the authorities -- an unavoidable circumstance for one who had led a double life -- and found the Soviet Union less than the worker's paradise Communist propaganda made it out to be. In any case, the affair of the Cambridge Five reinforced the suspicion that there was an active and dangerous Red "fifth column" in the West. In reality, the Red ideology that had been fashionable among the intelligentsia in the 1930s was losing its appeal, the idea that the USSR represented the way of the future becoming harder to maintain; there would still be traitors in the West, but increasingly they would only be in it for the money. [TO BE CONTINUED]
START | PREV | NEXT | COMMENT ON ARTICLE* SCIENCE NOTES: As discussed in AAAS SCIENCE NOW, Charles Darwin once noted that wild rabbits are hard to tame, but there is no animal more tame than a domesticated rabbit. Obviously the rabbit went through genetic changes in the course of its domestication, leading to the question of whether those changes were in a single or a few genes. Now a genetic analysis has shown that rabbit domestication is instead due to subtle changes in a suite of genes.

Rabbits were domesticated only relatively recently. About 1400 years ago, after a pope declared that they were "fish" that could be eaten during Lent, monks and others began to raise rabbits for meat and fur. These rabbits were derived from stock that lived only in Spain, Portugal, and southern France; the same strain of rabbits still live there today, providing a direct reference for comparison with domesticated rabbits.
A team from Uppsala University in Sweden performed the comparison. They collected and sequenced DNA from 14 wild rabbit populations, and from six domestic breeds. The study found that the rabbit genome is highly variable from one individual to the next, much more so than in humans -- but the genome comparison failed to reveal many consistent differences from the wild ancestor. Nima Rafati, a member of the Uppsala team, commented: "We did not find any evidence for [key] domestication genes. We propose that they may not exist."
The reality is that there are thousands of places in the genome where the frequency of certain versions of genes and other DNA differs between wild and domesticated rabbits. Many of these places are in regulatory DNA, which helps control gene activity; that DNA tends to be associated with brain and nerve cell development. Researchers have similarly been probing the history of sheep, dogs, horses, and other domesticated species, looking for DNA that helped make their wild ancestors more accommodating to people -- but the Uppsala researchers suggest they're not going to find any one gene or simple set of genes that account for domestication.
* If sleeping with the bedroom window open when the days are long and warm, one's rest can be disrupted by the insistent tweeting of birds preceding the sunrise. A study by a collaboration of ornithologists shows that birds that live in the city, where street lighting holds off complete darkness, will start tweeting earlier than their equivalents in the country -- European robins and blackbirds can start 90 minutes earlier. The effect wasn't as strong at dusk, the delay in shutting down being no more than ten minutes or so. Other than disturbing one's sleep, it's hard to see any real harm in the shift; since singing attracts mates, it gives birds more time to do so during the day.
* As reported by a note from SCIENCEMAG.org ("Long-lost Satellite Data Reveal New Insights To Climate Change" by Sid Perkins, 2 September 2014), in 2009 researchers at the National Snow & Ice Data Center of the University of Colorado in Boulder got wind of the existence of imagery taken by the US National Aeronautics & Space Administration's Nimbus satellites in the 1960s. The researchers were intrigued because the Nimbus satellites, flown originally to survey Earth's clouds in the visible and infrared, would have also captured images of sea ice.
The film had been stashed in warehouses in Maryland and North Carolina. The team obtained the film, and then tracked down the proper equipment to read and digitize its 16-level grayscale images, which had been taken once every 90 seconds or so. The imagery was then scanned and stitched together by software. So far, more than 250,000 images have been made public.
Nimbus 1, launched in 1964, was more or less a technology demonstrator, and it failed after less than a month in orbit. In that time, it was still able to return 27,000 images that provided a global snapshot of cloud and sea ice conditions. The images showed that the sea ice surrounding Antarctica in September 1964 covered about 19.7 million square kilometers (7.7 million square miles), more than the area of the US and Canada together, more than seen in any satellite data obtained from 1972 to 2012. However, data from a Nimbus satellite showed a record low coverage of sea ice just two years later. The data recovery project will end in 2015; the UC researchers also hope to use the data to extend satellite records of deforestation and sea surface temperatures.
COMMENT ON ARTICLE* SHELL GAME: As discussed in an article from THE ECONOMIST ("A Shot From The Dark"), 21st-century weapon systems have capabilities that would have been thought science fiction to the warriors of World War II. Take, for example, the Russian "VA-111 Shkval (Squall)" torpedo, a rocket-propelled weapon with a 210 kilogram (460 pound) warhead, a range of 11 kilometers (6.8 miles), and a staggering speed of more than 370 KPH (230 MPH). The only defense a warship has against it is to kill the launch platform before it gets within range.
For this reason, the West tries to keep tabs on who is buying the rocket torpedoes from Dastan Engineering, a Russian-owned enterprise in Kyrgyzstan. That is difficult, because the Shkval is not as big as a long-range missile, being 8.2 meters (27 feet) in length. It can be hauled around, concealed, by any large truck. There are an increasing number of such deadly and easily concealed weapons in circulation; the Russians have few qualms about selling them to anyone who can pay, since weapons are effectively Russia's only high-tech export.
The Russians are by no means the only players in the game. The Iranians, for example, have been clever in duplicating, and to a degree refining, weapons developed by the US, Russia, and particularly China. On 14 July 2006, Lebanese Hizbullah militants hit an Israeli Navy corvette steaming 15 kilometers (9.3 miles) offshore with an Iranian-made / Chinese-designed "C-802" antiship missile, killing four sailors and laying the warship up for major repairs. The corvette had countermeasures systems that could have defeated the weapon, but the Israelis didn't realize Hizbullah had it, and so the corvette's defenses hadn't been activated.
The C-802 is nothing particularly sophisticated, certainly not in the class of the Russian "Klub / 3M-54" or "Yakhont" antiship missiles. They can be launched from land batteries, aircraft, surface warships, and submarines; they have long range and smart target seekers. The Klub, codenamed "Sizzler" by NATO, flies to the target area under turbojet power and then performs a terminal attack with a Mach-3 "second stage", powered by a solid-fuel rocket engine. Countries publicly known to have the Klub or Yakhont include Algeria, China, India, Syria and Vietnam.
The USA tracks global shipping and so has a fair grasp of secret exports, though hardly a perfect one; countries with fewer resources can find themselves in the dark. Do the Iranians have the Shkval torpedo, or are they bluffing? Do the North Koreans have it? What makes the problem all the more difficult is the increasing "clandestinization" of munitions manufacture and transport. Factories that by all appearances are making commercial goods may also be making weapons, and weapon systems are being designed with concealment in mind.
A Moscow firm named "Concern Morinformsystem-Agat" offers the "Klub-K Container Missile System", consisting of four Klub missiles and an erector, with a control compartment for two operators, all stored inside a standard shipping container. To be sure, putting the weapon system inside a standard shipping container makes it easy to handle and transport, but it also provides camouflage, and turns any merchant ship, freight train, or heavy truck into a launch platform.

The Israelis are particularly concerned about advanced Russian weapons being funneled to Syria, with Israeli intelligence services working hard to map out the trade. Most munitions being sent to Syria are hidden in containers loaded up on merchantmen in commercial ports. Israeli spies have been competent at uncovering shipments of weapons and the Israelis have hit them with air strikes when they're found, but can they find them all?
Similarly, North Korea has become better at concealing the deployment of its missiles and other munitions. The Japanese have deployed a set of spy satellites with North Korea as the prime target; Japanese intelligence has a pretty good idea of North Korean capabilities, but the North Koreans are getting trickier, making spies on the ground more essential.
With increasing weapons sophistication and concealment, the threat is growing of the emergence of weapons that nobody knows about until it's too late. The result is tighter collaboration between nations on intelligence-gathering, as well more intensive work on surveillance and countermeasures systems. Countries that make such systems have growing sales opportunities, and so this low-profile arms race does have its benefits. That does not, however, reassure military forces who are likely to be downrange of the new weapons.
COMMENT ON ARTICLE* THE END OF AIDS? As discussed in an article from THE ECONOMIST ("Is The End In Sight?", 26 July 2014), in late July the 20th International AIDS Conference was held in Melbourne, Australia. Tragically, six delegates were killed when their airliner, MH17, was shot down over Ukraine on 17 July. However, the conference ended on an upbeat note, the conclusion being that the global AIDS pandemic could come to an end by 2030.
The notion of an "end" to AIDS is somewhat ambiguous, since anyone who has infected with the HIV virus can expect to be stuck with it for life. Optimists nonetheless believe that AIDS fighters now have the tools -- in particular, the antiretroviral (ARV) drugs which now keep around 13 million people alive -- to put the rate of new infections on a decline towards an effective endpoint of zero.
That will be an impressive achievement against a formidable adversary. A little more than three decades ago, HIV was unknown to science, but determined work has been turning the tide against AIDS. According to calculations by UNAIDS, the United Nations agency set up to deal with the disease, 1.5 million people died of it last year -- not good news, but down from a peak of 2.4 million in 2005. The rate of new infections has been falling for longer than that.
The notion that the rate can be reduced to zero by 2030 is ambitious, but still realistic. As Salim Abdool Karim, head of the Centre for the AIDS Programme of Research in South Africa, told delegates at the conference, many tools are now available to prevent HIV's transmission -- from counseling and condoms to drugs and circumcision (the foreskin of the penis is a major promoter of HIV infection). One of the most effective measures is, luckily, a side-effect of ARV treatment. ARVs help keep an infected host healthy by reducing the viral load; doing so also stops them from infecting others, a scheme referred to as "treatment as prevention".
A study published in 2011 showed that treatment as prevention works -- at least in the case of cohabiting couples where one partner is infected, with the likelihood of passing on the virus in that circumstance being reduced by 96%. How this special case translated into the broader one was unclear, but a paper published early in 2014, by a research group at the University of University of KwaZulu-Natal in South Africa, shows that uninfected people living in areas where 30% to 40% of those infected are on ARVs are 38% less likely to succumb to AIDs than those in places where ARV coverage is less than 10%.
ARVs are also increasingly being used by those who think themselves at risk to protect themselves. Such "pre-exposure prophylaxis (PEP)" has been talked of for a long time; it is now actually happening, thanks to the discovery that a drug named Truvada, a combination of the ARVs tenofovir and emtricitabine, is effective as a PEP treatment. Studies show that among gay men, use of Truvada reduces the risk of infection by 90%, and that it only needs to be taken four times a week to be effective -- meaning users can forget to take it daily on occasion and still be protected. The big problem with Truvada is that it's expensive, running to about $1,300 USD for a month's dose.
Truvada is notably spendy, but of course no measures to deal with AIDS are free, and there's no shortage of competition for public and private funds. Spending on prevention and treatment is about $19 billion USD a year in a combination of locally raised money and foreign aid at present; the level of funding is not expected to rise. That means doing more with less.
Eventually, effective ARVs will go off patent and become cheap generics, but that won't be for years or decades, and actions have to be taken now. One key is granularity. At one time, the world's AIDS maps recorded incidence only on a country-by-country basis; now they do so by regions, to zero in on the most badly afflicted locales. A recent study of AIDS in Kenya concluded that focusing on the worst-affected parts of that country could, over 15 years, reduce the number of new infections by 100,000 at no extra cost.
That granularity also applies to people. Researchers have long known that gay men, prostitutes, and intravenous drug users are at the highest risk, and so the more effort is required to deal with those groups. There are puzzles in such distributions -- for example, rates of infection in KwaZulu-Natal rise steeply for girls from age 15 to age 20, but not boys. It turns out that "sugar daddies", older men who like teen girls, are common in Africa, and end up being "superspreaders". Nobody's quite certain what can be done about that problem.
Still, some budgets will have to rise. A target to have 15 million people on ARVs by 2015 has turned out to be too small, one factor being that of the 35 million people estimated to be HIV positive, only about 16 million have been identified -- and they all need to be treated. Vaccines and cures have proven elusive, though work continues; even without them, however, the tools available will be enough, in time and given the will, to defeat AIDS.
COMMENT ON ARTICLE* ARIZONA ROAD TRIP (8): The core element of the Arizona trip was the airshow at Davis-Monthan Air Force Base. Getting up early as usual on Saturday, 12 April, after eating the free breakfast at the hotel, I decided to go to a Walmart to buy some flash memories. I'd located a Walmart to the east before leaving Loveland, but I got a surprise when I found it, since it was a "Neighborhood Market", a pure supermarket. Huh? Didn't know Walmart did such things.
I had to shrug, and then went south down Interstate 10 to Davis-Monthan for the airshow. I made another error then, thinking the gates opened at 8:00 AM, but the time was actually supposed to be 9:00 AM. With nothing much to do to kill an hour, I recalled I had mapped a Walmart on Interstate 19 to Nogales, Mexico, so I decided to double back on I-10 and then take a jog south on I-19. Actually, one error fixed another, since I found a Walmart not far away on I-10. I went in and bought a 32 GB flash SD card and a 32 GB flash USB stick. It cost me a bit over $50 USD; I could have probably gotten them for about ten dollars less via Amazon, but I had an immediate need, and the ten bucks was nothing.
That done, I went back to Davis-Monthan to queue up in the gate line. To no surprise, it was congested, but in about a half-hour or so I was parked in the corner of a field -- good location, easy to find my car again. I walked through the field and through the security line at the gate, the airmen being polite and efficient. I went down the flight line to take shots of the aircraft on display: an A-10 Warthog close-support aircraft along with ordnance, C-17 Moose, KC-135, RC-135, B-52H, AC-130 Spectre gunship, B-1 bomber, C-5 Galaxy.

While I was taking a shot of the B-1, I realized that even though I wasn't so far away from it, it still fitted into the Lumix camera's field of view. I suddenly realized that the disappointments I had concerning camera zoom in the past were due to a subtle misunderstanding of what zoom does. My notion had been that it was supposed to bring far-away objects up close, but that's not exactly the truth. What zoom does is merely zero in on a section of the field of view; the Lumix could have 60x zoom because its default field of view is very wide.
True, zoom does give an effective magnification, but if the object can't be seen clearly with the naked eye, zooming in simply blows up an unclear image. A camera with a low zoom and relatively narrow field of view will bring an image in just as close. The real trick of zoom is selectivity -- being able to pick out large or small parts of a scene.
The Tucson Police Department and the US Customs & Border Protection agency were well-represented on the flightline with helicopters, fixed-wing aircraft, and ground vehicles. I went up to a cop with a dog, what turned out to be a Belgian malinois, the dog being engaged in a stubborn tug-of-war with an airman over a training "chew toy" on a cord. I later looked up the malinois and found that the breed generally looks like a German shepherd, sometimes being known as a "Belgian shepherd", but with lighter build. This one didn't fit that pattern -- the physique was right, but it was mostly black and a shorthair.

The malinois was actually a pretty friendly dog for a cop dog, but it was not going to give up its grip on that chew toy for anything -- I tried to sneak it out of its mouth, it glared and growled at me. On considering the beast, I realized that, if set loose on a troublemaker, it would chomp down on a limb and not let go until told to release, or killed. It wasn't such a big dog, but it would keep a subject busy until the cop could take him down and cuff him. There would no doubt be a certain messy amount of blood involved.

I checked out more gear as I went down the flight line -- I was particularly interested in the BMW motorbikes operated by the Arizona Highway Patrol, never have seen such in police hands. I then turned right to walk down the flightline in front of the hangars. All the exhibits there were in shelters that I found puzzling at first: they were just big open rectangular metal frame boxes, with canvas providing a roof and partial sides, but open front and back. I didn't have to think very long to realize that in mid-summer, working on an aircraft sitting in the direct sun would be impossible, with a prospect of being burned by putting a bare hand on metal.

I went down the line in front of the hangars, getting shots of Air Force jets, helicopters, classic warbirds, motorbikes, hot cars. I got a kick out of a MiG-17 fighter with the name BORIS written on it in cyrillic text, along with a cartoon of Boris Badenov throwing a bomb. Once I got to the end of the line, I stood there for a moment, noticing how well the insole cushions I'd put in my shoes worked: I'd pounded a lot of ground on hard pavement, but my feet felt little the worse for wear for it. I did end up with a sunburn around my collar, the only part of me unprotected from the Sun; I know better than to wear a short-sleeved shirt to an airshow. [TO BE CONTINUED]
START | PREV | NEXT | COMMENT ON ARTICLE* THE COLD WAR (36): American troops in the war theater served a tour of duty determined on an individual basis, with soldiers accumulating "points" towards their eventual transfer out of the line of fire. The points system did not encourage initiative, men becoming ever more risk-averse as they became "short-timers", fearful of being wounded or killed just before they were to leave. That was understood by the military, but the belief was that it was the most just scheme under the circumstances. British forces, in contrast, rotated troops by regiment, an approach that promoted unit solidarity.
American troops could look forward to stints of "R&R (rest & relaxation)" in Japan. A soldier's pay went far in Japan, which had been impoverished by the defeat in World War II; the Japanese might not have much cared for the carousing of drunken Americans, nor for the prostitution of Japanese women in their service -- but the money was welcome, and the polite Japanese made the outsiders feel as welcome as possible under the circumstances. One American enlisted man remembered his R&R in Japan in glowing terms: "It was the land of the big PX. You drove to the Hotel Sun, got a girl, a room, and all the beer you could drink for five days for sixty dollars. I fell in love with Japan."
The perception of Japan as a pleasant vacation spot helped diffuse, if not completely eliminate, the bitter American hatred for the "Japs" that had marked the war in the Pacific. More substantially, as a forward staging area, Japan benefited enormously from the war. Under an exercise blandly labeled "Special Procurements", the US pumped billions of dollars into Japan to obtain material and services -- the amount of money being comparable to that provided to West Germany under the Marshall Plan. Schemes to dissolve the "zaibatsu", the big prewar Japanese companies, were shelved. The business generated by the conflict did much to restore Japan's economic fortunes, and lay the foundation for an eventual economic boom.
The war did have the negative effect that the Japanese Left, which had come under increasing pressure as the Americans became more anti-Communist, was more or less suppressed; postwar Japan was a democracy, but it was a skewed one, tilted towards the conservative -- colored by the prewar mindset that the citizens were beholden to the state, not the other way around. The Americans were primarily concerned with fighting Communism; as long as Japan was aligned with that mindset, the Americans weren't too concerned about how the Japanese did things.
In addition, although the American occupation government had suppressed Japanese militarism, Article 9 of the postwar constitution renouncing the use of force as a means of furthering Japan's ambitions, Japan ended up re-arming, at least to a degree. The formal peace treaty of September 1951 provided American military security guarantees to Japan, coupled with steps taken to rebuild Japan's military capability -- emerging in mid-decade as the "Self-Defense Forces (SDF)". The SDF was a somewhat unusual military force, organized along strongly defensive lines, with offensive capability strongly avoided. Japanese militarism had led the country down the road to disaster, having taken on a war that Japan could not win, and the Japanese people would not soon forgive the militarists for their folly. [TO BE CONTINUED]
START | PREV | NEXT | COMMENT ON ARTICLE* GIMMICKS & GADGETS: In May 2011, the City of New York awarded a contract to Nissan Motors to provide a "standard" new-generation taxicab that would equip NYC's taxi fleet of over 13,000 vehicles. The city government's idea was that, by requiring taxi operators to obtain the same model of vehicle, the purchase price would be lower, and amenities of the cabs would be standardized. There were legal protests against the measure, but the courts eventually rejected them all.

The Nissan NV200, AKA "Taxi of Tomorrow", is much more functional than pretty, and it uses ordinary internal-combustion instead of hybrid propulsion -- though a hybrid is in the works. However, there's still much to like about the NV200:
So the NV200 looks like a pretty good deal. Not that it's so important: everyone knows real New Yorkers always take the subway.
* Dogs have a long and honored history of service in disaster relief. They have keen senses that can seek out, say, victims of an earthquake buried in rubble; they are also generally eager to please, readily trained, and not hard to care for. While there's been considerable work on machines to help in disaster relief, none so far seem as generally useful as the reliable dog.
But what if we could get the best of both? A multi-institution research collaboration is now working on the "Smart Emergency Response System (SERS)", which envisions humans, dogs, and robots wired together to save people in an emergency. One component of SERS is focused on developing harnesses for rescue dogs loaded with sensors and communications links. The harnesses can be fitted with microphones, cameras, and other sensors as per the particular emergency to be dealt with; they also include a heart-rate monitor and other sensors to monitor the condition of the dog, as well as speakers and vibration devices to give commands to the dog.
The exercise is still in the testing phase, but researchers involved think their work has great potential. Indeed, it sees plausible that gadget-happy pet owners like to kit their dog up with a techno-vest, if just because they like the idea of owning a cyborg dog. Incidentally, for those who want to get their feet wet right away in digitally enabling their dogs, GoPro is now selling a harness that will allow a dog to carry a GoPro camera. The mind boggles.
* As discussed in a note from WIRED.com, it is common for computer users to own a range of machines -- at least a smartphone and a laptop, often a tablet and a desktop as well. Although few envisioned it, users are finding that using two of their computers together gives a whole greater than the sum of its parts.
Many people have adopted the multi-screen approach to beat back distraction -- doing work on a laptop, while leaving social apps like Twitter on a tablet; or using the tablet to screen inputs and calendar alerts. It turns out that, counter-intuitively, using multiple devices can help focus attention, instead of disperse it. A pile of browser tabs on a laptop becomes mentally confusing; tasks get hidden, and maybe forgotten. It's much easier to keep track of tasks if they're listed on a separate screen. It's like having several sheets of paper around on a desk, with the comparison becoming more apt as computing devices become more like clipboards, each with its own "paper" clipped on.
COMMENT ON ARTICLE* HELICOPTER FLATTOPS RULE THE WAVES: Although the US military has been on a budget diet as of late, it hasn't been brought to a stop by any means -- one example being the USS AMERICA (LHA-6), a US Navy amphibious assault ship, the first in its class. It put to sea for the first time in 2013 and is now undergoing shakedown.
Anyone casually looking over the AMERICA would immediately think: "Aircraft carrier!" -- and it clearly is, at a length of 257 meters (844 feet) being about the same size as the famous fleet carrier USS ENTERPRISE of World War II. However, although it certainly carries aircraft, in a sense it's a landing vessel, or more strictly a command ship and landing vessel, intended to operate as the flagship of an amphibious assault force. The force commander can use its communications and other facilities to direct the operation, while putting its complement of Marines ashore with its helicopters or Osprey tilt-rotors. It can also carry a handful of F-35B short-takeoff / vertical landing (STOVL) strike fighters to support the troops on the beach.

The AMERICA is an evolutionary product of a series of amphibious assault ships, being a modification of the earlier USS MAKIN ISLAND, an advanced variant of the WASP class. The MAKIN ISLAND's primary advance over earlier WASP-class vessels is a hybrid propulsion system, in which the ship's twin props are either driven by two gas turbines, at high speeds; or by two electric motors, at low speeds, the electric motors being powered by diesel generators at the heart of the ship's electrical power system. All earlier WASP-class vessels used steam propulsion, which was substantially more troublesome to maintain, harder to automate, and more expensive on a life-cycle basis. The new "hybrid" scheme is much more fuel-efficient than steam propulsion.
The AMERICA improves on the MAKIN ISLAND by rearranging internal spaces to provide more hangar room for the Osprey and F-35B, which are larger than the flying machines carried by the MAKIN ISLAND. The AMERICA does not have a well deck for handling landing craft and amphibious vehicles; it was sacrificed for larger hangar spaces and more aviation support. Other vessels in an amphibious task group will handle landing craft and amphibious vehicles.
The AMERICA has a complement of 65 officers, 994 enlisteds, and 1,687 Marines. No mention is made of crew comforts in press releases, suggesting accommodations are austere, though it does have an onboard hospital and desalinization system. It has defensive systems, including countermeasures and:
_________________________________________________________________________ twin Rolling Airframe Missile (RAM) launchers to defeat antiship missiles twin Phalanx gatling cannon for last-ditch antiship missile defense twin Evolved Sea Sparrow launchers for air defense seven dual 12.7 mm (0.50 cal) gun mounts _________________________________________________________________________
A typical air asset complement would be:
_________________________________________________________________________ 12 Ospreys 6 F-35Bs 4 CH-53K heavylift helicopters 7 TwinCobra gunships 2 Knighthawk rescue helicopters _________________________________________________________________________
The AMERICA could also be used as an auxiliary assault carrier, with 20 F-35Bs and two Knighthawks. It will be handed over to US Navy later in 2014, to be based in San Diego.
* As noted here last September, Japan also operates helicopter carriers, but so far hasn't been interested in obtaining the F-35B to fly off of them. AVIATION WEEK discussed that option, saying the first two, HYUUGA and ISE, could operate the F-35B, but the vessels would be marginal for the job, lacking adequate hangar and deck space. However, the new and bigger IZUMO, which is to be followed by a sister ship, is big enough to do the job. It would require some refit, the vessels requiring command-control-communications facilities for fast jet operations, as well as a ski-jump ramp: the F-35B cannot realistically take off vertically with a reasonable warload, but can get off the deck when heavily laden with no real fuel penalty with a ski jump.

Again, Japan has not expressed interest in obtaining the F-35B, but given current tensions with China and a more assertive posture by the government of Prime Minister Abe Shinzou, that could change. The Japanese are very interested in obtaining the Osprey, which the US has considered giving an attack capability.
COMMENT ON ARTICLE* FRANCE IN AFRICA: Although Europeans in general tend to be wary of military adventurism, the French, as is often the case in other regards, are something of an exception. They retain a certain interest in their ex-colonies in central Africa, which are currently under active or potential threat from Islamic insurgency.
Francois Hollande, the current French president, took office in 2012 knowing little about Africa. He started up the learning curve in 2013 when he sent troops into Mali, as discussed here at the time. Operation SERVAL appeared to be a success, but it was then followed by turmoil in Mali's government and a flare-up of insurgency in the Central African Republic (CAR), with more French troops being sent in. Having found problems growing instead of fading out, Hollande has become increasingly focused on Africa -- as demonstrated by his tour of Ivory Coast, Niger, and Chad in mid-July.
The trip was presented as business-oriented, and it was, but the pressing issue was collective security. France wants to reorganize its military presence in the region, under the banner of Operation BARKHANE, as a 3,000-strong counter-terrorism force. The new force will be permanent, with its headquarters in Chad's capital, N'Djamena. It has been set up to cover five countries: Burkina Faso, Chad, Mali, Mauritania, and Niger, all former French colonies. A thousand French soldiers will remain indefinitely in Mali, down from a peak of over 4,000 in 2013, focused on counter-terrorism operations in the north. Another 1,200 will be stationed in Chad, the rest being divided between a surveillance base in Niger, a bigger permanent base in Ivory Coast, and some special forces in Burkina Faso. BARKHANE will be supported by 20 helicopters, 200 armored vehicles, ten cargolift aircraft, six fighter planes, and three drones.
Malian security is now in principle being taken over by a 6,500-strong United Nations stabilization force known by its French acronym, MINUSMA. However, the handover has been slow and uncertain, being delayed in particular by the resurgence of fighting between Malian troops and Tuareg separatists in northern Mali.
The French are even more bogged down in the CAR. Their mission there had a clearly humanitarian aspect, the fighting having involved massacres by armed Muslim and Christian groups that threatened to escalate into genocide; however, the intervention also had the strategic goal of restoring order to a mineral-rich landlocked state whose troubles might easily spread to neighbors. Unfortunately, the violence continues in the CAR, a UN report describing the country as "de facto partitioned". A UN stabilization force is expected to arrive there as well, but nobody is certain when French troops will be able to leave.
Although the magnitude of the challenge is growing, the French reaction is nonetheless limited, as consistent with long-range policy. In 2008, under Nicholas Sarkozy, Hollande's predecessor as president, a defense review concluded that France's primary interest was in a "strategic arc" of instability from North Africa through the Horn of Africa into the Gulf. That didn't mean abandoning the states in the middle of Africa, but it did mean reducing the French footprint there, giving up mutual defense pacts and focusing instead on border security and counter-terrorism. To this end, Sarkozy closed one of the three permanent French military garrisons in sub-Saharan Africa, in Senegal, and opened a new one in Abu Dhabi.
The fall of Libyan dictator Muammar Qaddafi in 2011 helped promote insecurity in the region, with the trouble focused on a desert "highway" from the porous borders of southern Libya through the Sahel to the Atlantic. Along it flow arms, drugs, illegal immigrants, and jihadists. The French want to break up the terrorist networks in the region, which periodically grab French citizens for ransom. That means a de-emphasis on "heavy metal" combat formations, there being no need for massive firepower, towards forces that are relatively lightly armed but are highly mobile.
There have been frictions between the French and the British, who haven't appreciated French meddling in the security situation in Nigeria, previously a British colony, while largely bypassing the UK. That sounds like a problem that will be fixed sooner rather than later, since the British and French have a common interest in protecting the region from jihadism. The Americans, having their own issues with Islamic militancy, are discreetly throwing in their support for the fight against African jihadism. Indeed, given the general upward trend in Africa, there's reason for confidence that the jihadist threat can be controlled, even eliminated. Unfortunately, there's no telling when that might happen.
COMMENT ON ARTICLE* ANOTHER MONTH: As discussed in an essay in BLOOMBERG BUSINESSWEEK, the USA has passed "peak gun": after a surge in gun sales from 2009, from 2013 gun sales have fallen dramatically, leaving American gun makers struggling with red ink.
Why the surge? Why the collapse? One word: Obama. When Barack Obama was elected president in 2008, there was a widespread fear that a liberal president would seize everyone's guns -- which led to a buying spree of guns, focused on assault rifles, seen as the weapons most likely to be banned. Okay, the Obama Administration did little or nothing about gun control during its first term, but gun enthusiasts weren't fooled: once Obama got a second term and didn't have to worry about re-election, of course then he'd clamp down.
In the wake of the 2012 school shootings in Newton, Connecticut, the Obama Administration did make a push on gun control, which sent purchases up through the roof. However, the Obama gun control effort was a fizzle, with the administration, and many of the public leaning towards gun control, realizing the game was unwinnable. The conclusion was that it was not worth the bother to try any longer -- all the more so because, as discussed here in 2013, despite occasional berserk shooting sprees, violent crime rates are clearly in long-term decline. There's less incentive to disarm.
There's equally less incentive to arm, and the binge also had the effect of saturating the market for guns. They tend to last a long time, often being passed down through generations; having stocked up on firearms, enthusiasts had little interest in buying more. The gun industry has long feared the government moving against gun sales. It is a particular irony to find the gun industry in pain for no more reason than that the government isn't so worried about the matter any longer.
* As discussed in an AP article ("Sesame Catching On In Southeast US" by Kelly Kissel, 29 August 2014), although the US Southeast is stereotyped as the "land of cotton", farmers are of course primarily concerned with raising crops that make them the most money -- and as of late, they've been getting into sesame.

Sesame not only fetches a fair price and is cheaper to raise than cotton or soybeans, it also is drought tolerant, and the latest varieties can be harvested by conventional agricultural gear. Thousands of acres from Arkansas to Florida are now being planted with sesame, often in a rotation with cotton, soybeans, and corn, sesame being particular well-suited to fields far from irrigation lines. In places where deer are common, it also has the advantage that deer won't eat it.
The nation's traditional sesame-growing region is in western Oklahoma and Texas. The Southeast is actually better suited to the crop, rainfall patterns being more accommodating to sesame there. It has no chance of being a primary crop, being only planted in tens of thousands of acres, compared to the millions for cotton, soybeans, sorghum, or corn -- but it is suited for marginal fields not so good for raising those crops.
One traditional difficulty with sesame is that the seed pods split open on maturity and scatter of seeds on the ground -- leading some linguists to debate whether this led to the password "open sesame" in the book "Ali Baba and the 40 Thieves." Over the last decade, varieties with shatter-resistant pods have become more common, which allow farmers to leave sesame unharvested while they bring in more weather-sensitive crops. Farmers can then adjust their combines to strip the pods from sesame plants, the pods being left whole to contain their oil. After harvesting, the pods are obtained by Sesaco -- America's sesame company, actually controlled by Mitsubishi of Japan -- with the seeds ending up being compressed for oil, or dried for use as a food additive or condiment, such as on buns. Says one sesame farmer: "We just tell everybody: EAT HAMBURGERS."
* Wikipedia got into a flap with British photographer David Slater, who was on a visit to Indonesia in 2011 when a monkey got hold of his camera. The monkey was fascinated with the shutter button and kept pressing it over and over, ending up taking a self-portrait. Wikipedia ran the photo, doing no more than crediting the anonymous monkey; Slater insisted that he had the copyright on the photo, and Wikipedia was violating his copyright.
A tricky legal case? Not really. Slater was not the author of the photo, the monkey was -- the fact that Slater owned the camera was irrelevant. The monkey was in no position to assert rights, and since no rights could be asserted, the photo was in the public domain. One might be able to argue that, if the monkey had been in a government-run park, it was a ward of the state, and the park agency could accordingly assert rights on behalf of the monkey. It would be unlikely that anyone would consider it worth their substantial bother to try, however.
* Thanks to three readers for their donations to support the websites last month. It is very much appreciated.
COMMENT ON ARTICLE